Black Hat Arsenal USA 2018
We got chance to present Archery tool in world largest conference BlackHat USA 2018 Arsenal at Las Vegas. It was great experience in front of huge audience.

We released new and stable version of Archery tool Archery-v1.0. We’re working to solve the challenges in VA/VM and make a great tool for Vulnerability Assessment and Management tool that help info sec professionals and Developers.
It has been a great chance to interact with multiple security professionals at BlackHat USA this year and discussed with them about challenges facing while doing Vulnerability Assessment and Management.
Here is the key features released in Archery v1.0:
Dynamic Authenticated Scanning:
Web Dynamic Authenticated Scanning: Archery help you to perform web application dynamic authentication using inbuilt selenium integrated solution. Archery storing application authenticated cookies value into cookies_db and using ZAP Replacer its replace cookies value from headers. It’s also using selenium based authentication and grab cookies value runtime.
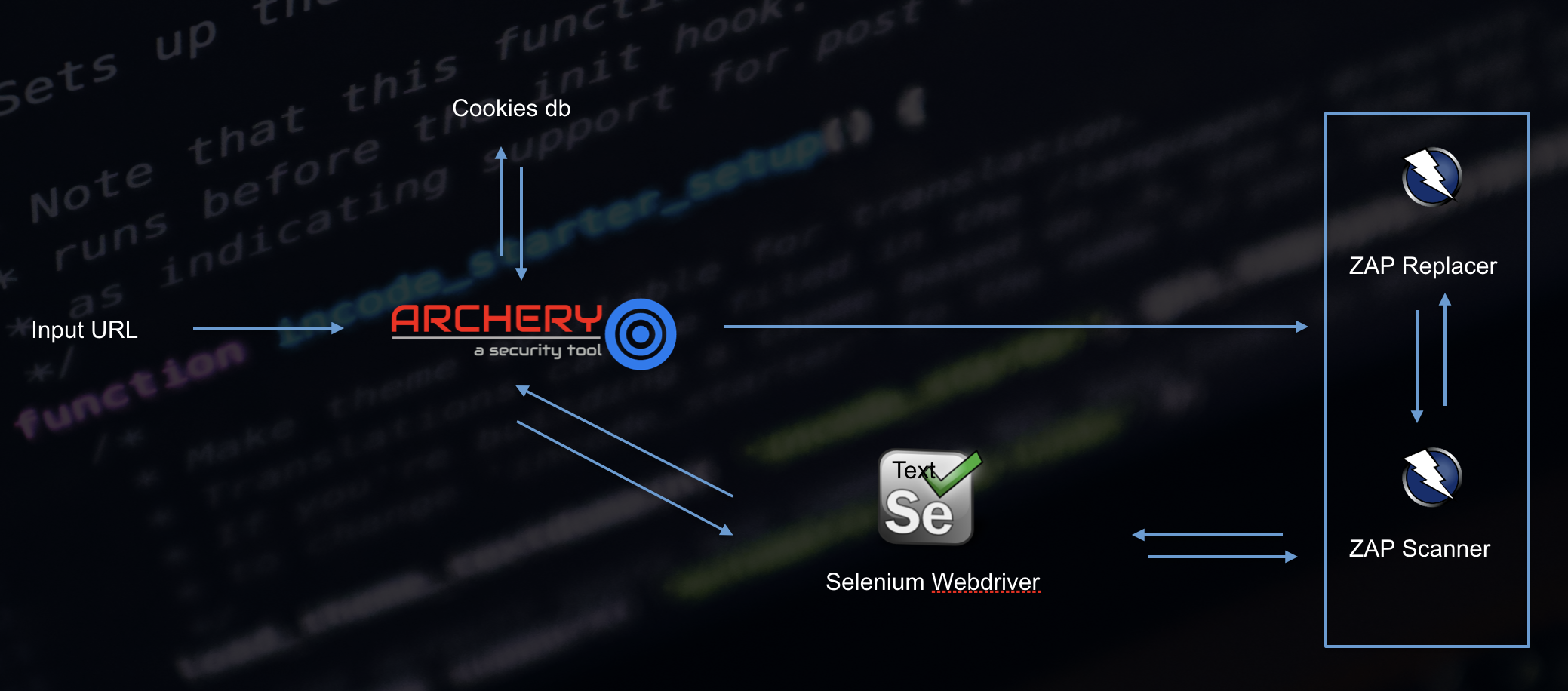
Web application Dynamic Authentication Solution by Archery.
JIRA Ticketing
Archery has JIRA Ticketing system plugin that you can plug with Archery tool and raise tickets.
JIRA Ticket Integrated and raise vulnerability ticket..
After JIRA Ticket raised issue tracking..
False Positive Vulnerability Tracking
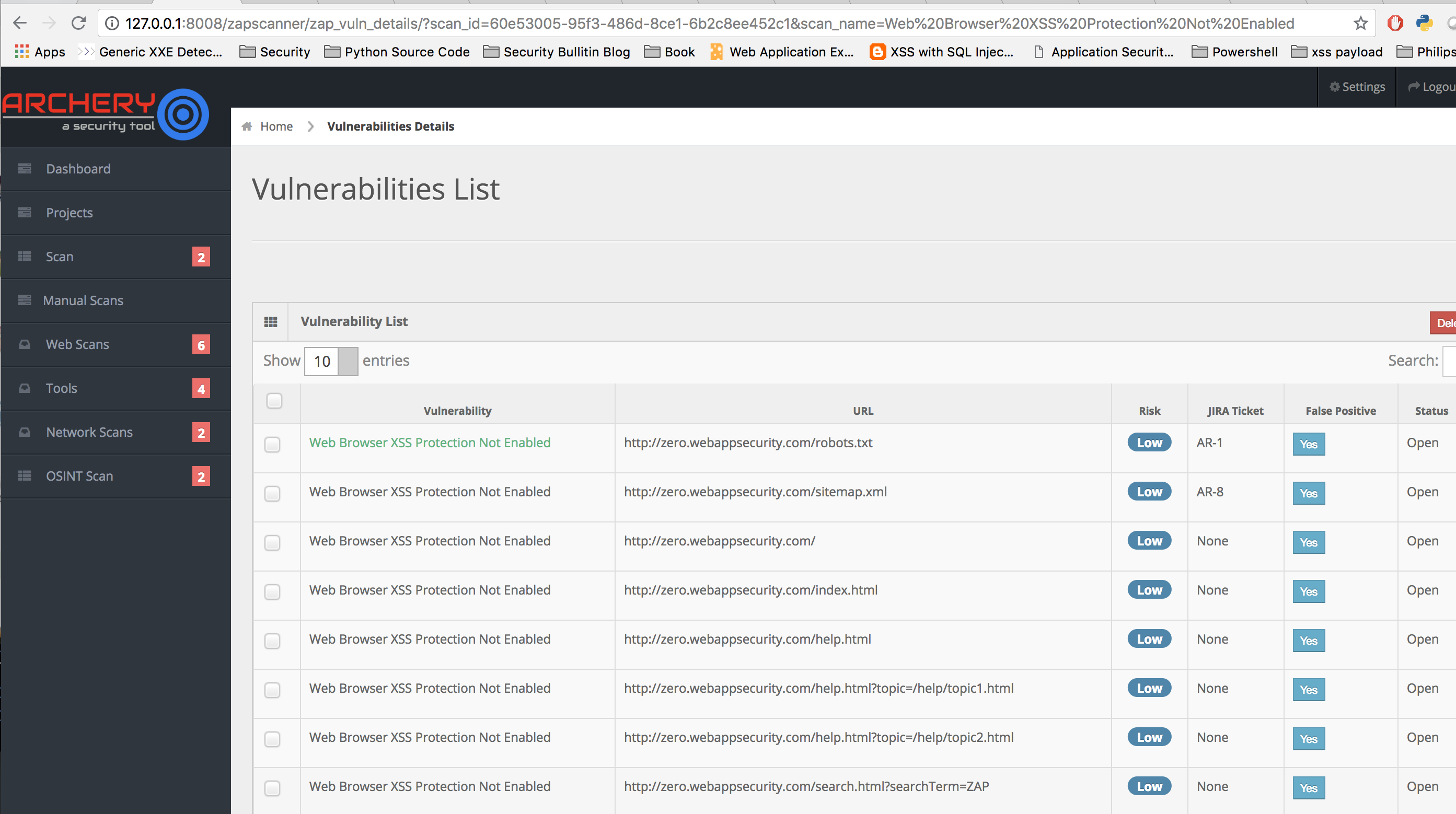
Archery help you on removing false positive vulnerabilities after scan completion. Its very important to remove false positives vulnerabilities and work on new discovered vulnerabilities from all future scans.
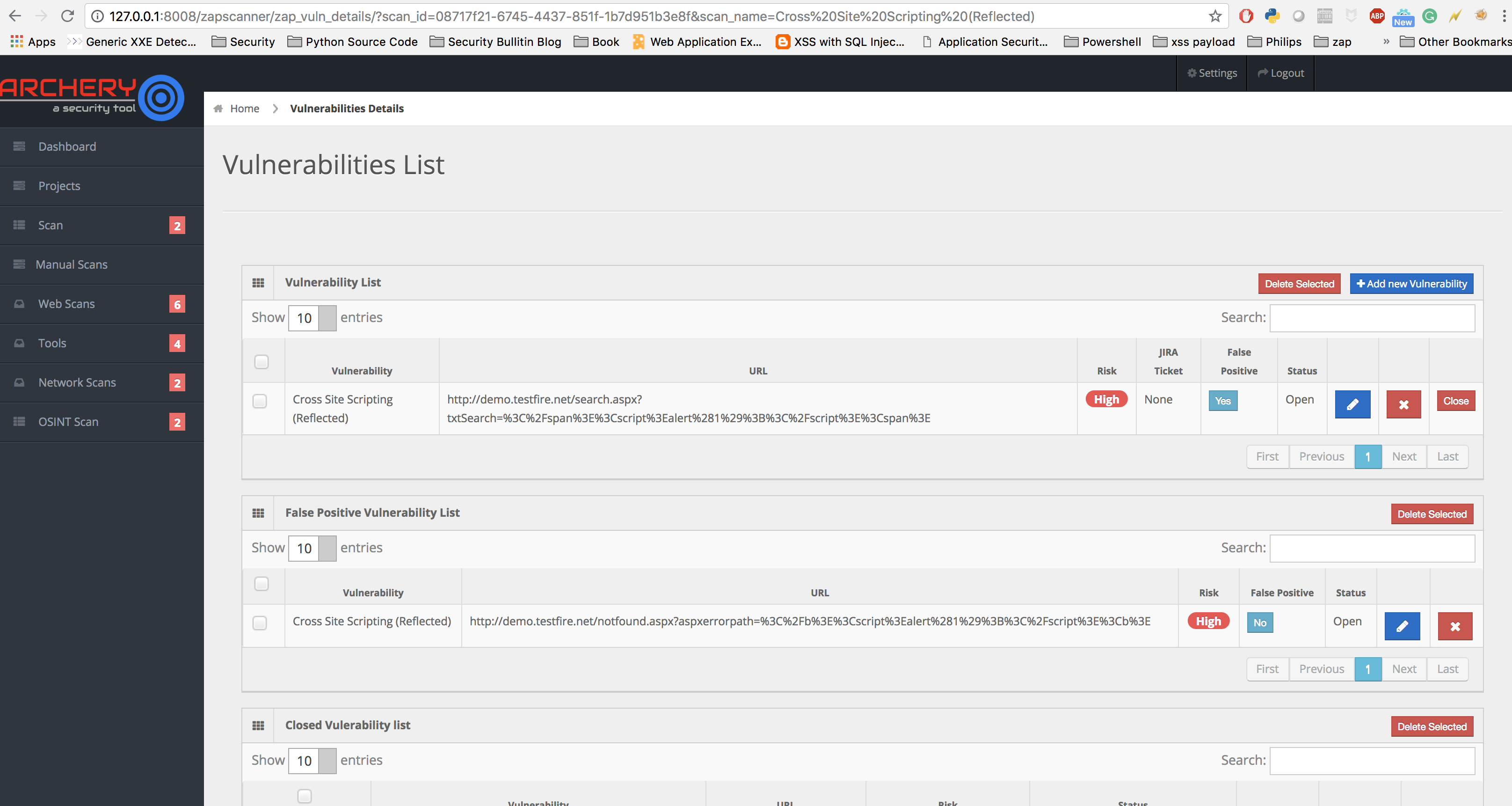
False Positive marked vulnerability.
Below are the change logs:
- Nmap Vulners.
- JIRA Ticketing.
- Concurrent Scans.
- SSL Tool integration.
- Nikto Tool integration.
- Sub Domain Scanning.
- ZAP scan report parser.
- Burp scan report parser.
- Nessus scan report parser.
- Arachni scan report parser.
- Acunetix scan report parser.
- Duplicate vulnerability mark.
- Netsparker scan report parser.
- Webinspect scan report parser.
- False Positive vulnerability mark.
- False Positive Tracking Dashboard.
If you want to contribute, please visit our Github and follow instructions.
We got chance to present Archery tool in world largest conference BlackHat USA 2018 Arsenal at Las Vegas. It was great experience in front of huge audience.

We released new and stable version of Archery tool Archery-v1.0. We’re working to solve the challenges in VA/VM and make a great tool for Vulnerability Assessment and Management tool that help info sec professionals and Developers.
It has been a great chance to interact with multiple security professionals at BlackHat USA this year and discussed with them about challenges facing while doing Vulnerability Assessment and Management.
Here is the key features released in Archery v1.0:
Dynamic Authenticated Scanning:
Web Dynamic Authenticated Scanning: Archery help you to perform web application dynamic authentication using inbuilt selenium integrated solution. Archery storing application authenticated cookies value into cookies_db and using ZAP Replacer its replace cookies value from headers. It’s also using selenium based authentication and grab cookies value runtime.
 |
|---|
| Web application Dynamic Authentication Solution by Archery. |
JIRA Ticketing
Archery has JIRA Ticketing system plugin that you can plug with Archery tool and raise tickets.
 |
|---|
| JIRA Ticket Integrated and raise vulnerability ticket.. |
 |
|---|
| After JIRA Ticket raised issue tracking.. |
False Positive Vulnerability Tracking
Archery help you on removing false positive vulnerabilities after scan completion. Its very important to remove false positives vulnerabilities and work on new discovered vulnerabilities from all future scans.
 |
|---|
| False Positive marked vulnerability. |
Below are the change logs:
- Nmap Vulners.
- JIRA Ticketing.
- Concurrent Scans.
- SSL Tool integration.
- Nikto Tool integration.
- Sub Domain Scanning.
- ZAP scan report parser.
- Burp scan report parser.
- Nessus scan report parser.
- Arachni scan report parser.
- Acunetix scan report parser.
- Duplicate vulnerability mark.
- Netsparker scan report parser.
- Webinspect scan report parser.
- False Positive vulnerability mark.
- False Positive Tracking Dashboard.
If you want to contribute, please visit our Github and follow instructions.